The network of power plants and lines connecting to homes and businesses is widely considered to be among the most critical infrastructure in the world, especially in advanced economies. It’s also one of the most frequently attacked, with consequences that could potentially reach far beyond the power sector.
Many countries across the globe have classified electrical infrastructure as critical to a functioning society. The US government labels energy as one of 16 critical infrastructure sectors considered so vital that “their incapacitation or destruction would have a debilitating effect on security, national economic security, (and) national public health or safety.” In particular, the power sector is seen as uniquely critical for the “enabling function” it provides across all critical infrastructure sectors. If the power went out across a large region for an extended period, highly dependent systems—such as financial, communications, transportation, water, and sewer networks—would be severely impacted, leaving the population immobile, incommunicado, and in the dark. In a word, vulnerable.
Much ado about something: Growing cyber risk in the power sector
Energy is one of the top three sectors targeted for attack in the United States. In 2016 alone, the sector reported 59 incidents, 20 percent of the 290 total incidents reported in that year. Only two other sectors reported more incidents—critical manufacturing and communications. This, however, is not specific to the United States alone—the sector has been a prime target in Europe and Japan; in Australia, it was identified as the sector with the highest number of reported incidents or near-incidents related to critical infrastructure. What’s more, electric power companies report a continuous barrage of attempted intrusions, and though most fail, activity is accelerating. US Energy Secretary Rick Perry commented that such intrusions are "happening hundreds of thousands of times a day.” And in early 2018, there was “an extreme uptick” in cyberattacks targeting the electric grid in North America.
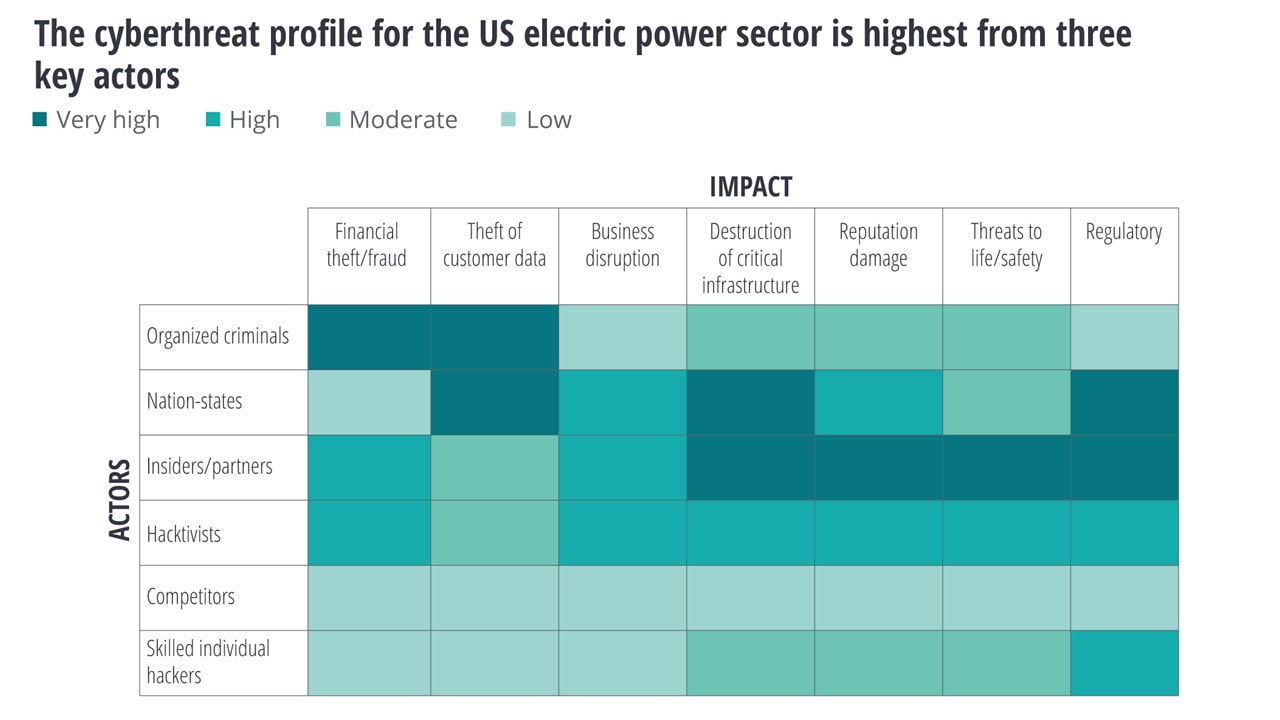
Not only are attacks rising, but cybersecurity experts and intelligence sources report that the number of threat actors is increasing and their capabilities expanding. Internal threats due to human error, disgruntled employees, or contractors have typically been one of the most common threats. But nation-states and organized crime are becoming more active, and most disturbingly, could be intersecting. Nation-state actors are believed by some to be contracting with organized crime groups, possibly to ensure deniability. The problem can be compounded as hackers with little institutional or technical knowledge can increasingly access sophisticated tools on the dark web, which operates outside of the traditional internet. This threat profile typically changes over time and from country to country.
Many countries across the globe have classified electrical infrastructure as critical to a functioning society. The US government labels energy as one of 16 critical infrastructure sectors considered so vital that “their incapacitation or destruction would have a debilitating effect on security, national economic security, (and) national public health or safety.” In particular, the power sector is seen as uniquely critical for the “enabling function” it provides across all critical infrastructure sectors. If the power went out across a large region for an extended period, highly dependent systems—such as financial, communications, transportation, water, and sewer networks—would be severely impacted, leaving the population immobile, incommunicado, and in the dark. In a word, vulnerable.
Much ado about something: Growing cyber risk in the power sector
Energy is one of the top three sectors targeted for attack in the United States. In 2016 alone, the sector reported 59 incidents, 20 percent of the 290 total incidents reported in that year. Only two other sectors reported more incidents—critical manufacturing and communications. This, however, is not specific to the United States alone—the sector has been a prime target in Europe and Japan; in Australia, it was identified as the sector with the highest number of reported incidents or near-incidents related to critical infrastructure. What’s more, electric power companies report a continuous barrage of attempted intrusions, and though most fail, activity is accelerating. US Energy Secretary Rick Perry commented that such intrusions are "happening hundreds of thousands of times a day.” And in early 2018, there was “an extreme uptick” in cyberattacks targeting the electric grid in North America.
Not only are attacks rising, but cybersecurity experts and intelligence sources report that the number of threat actors is increasing and their capabilities expanding. Internal threats due to human error, disgruntled employees, or contractors have typically been one of the most common threats. But nation-states and organized crime are becoming more active, and most disturbingly, could be intersecting. Nation-state actors are believed by some to be contracting with organized crime groups, possibly to ensure deniability. The problem can be compounded as hackers with little institutional or technical knowledge can increasingly access sophisticated tools on the dark web, which operates outside of the traditional internet. This threat profile typically changes over time and from country to country.
One of the most common attack vectors in the power sector is phishing, or attacks launched via email asking users to click on a link that then injects malware into their systems, or via email asking for personal data to enable unauthorized network access. In 2017, out of 226 cyber bulletins posted by the US Electricity Information Sharing and Analysis Center (E-ISAC) on its portal, over 30 percent involved phishing. Other common attack vectors include “watering hole,” credential theft, denial of service, and remote access trojans.
Attackers set sights on ICS and third parties
Power companies have long been aware of growing cyber risk, and were one of the first industries to respond, with requirements to implement cybersecurity controls through the North American Electric Reliability Corporation’s Critical Infrastructure Protection (NERC-CIP) standards, initiated in 2007. Nonetheless, the threat continues to evolve, as attackers home in on industrial control systems (ICS) and attempt to access them through third parties in the power sector supply chain.
Targeting ICS blurs line between cyber- and physical attacks: In another unsettling but growing trend, cyberattackers are increasingly targeting industrial control systems (ICS), sometimes potentially laying the groundwork to do physical damage to the grid. Previously, attackers primarily targeted utilities’ information technology (IT) systems to steal data or launch ransomware for financial gain. The threat is now becoming even more insidious, with reports of hackers tied to nation-states and organized crime trying to burrow their way into utility ICS, seeking to learn how systems operate, and positioning themselves to control critical physical assets, such as power plants, substations, transmission, and distribution networks, and to potentially disrupt or destroy them.
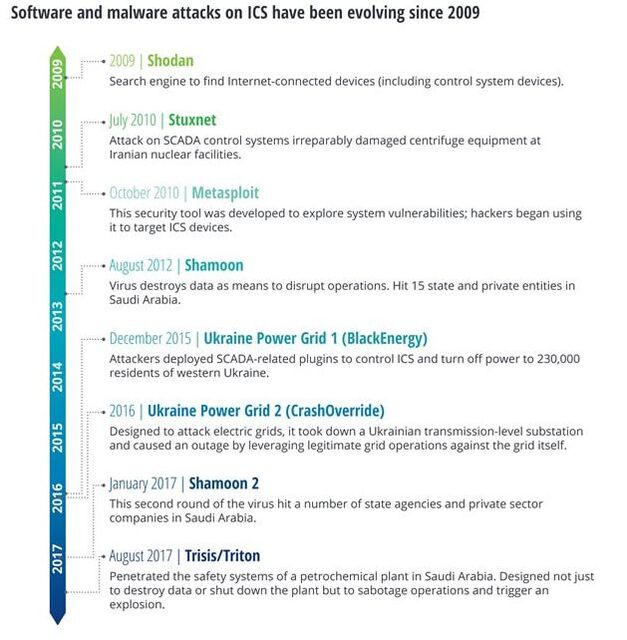
This targeting of ICS, which has developed over a decade, is blurring the lines between cyber- and physical attacks, prompting national security concerns in many countries. ICS attacks have evolved in scope and purpose across the globe. Attackers began by exploiting software developed for legitimate purposes, such as Shodan and Metasploit, to find components and devices connected to the internet, and to target supervisory control and data acquisition (SCADA) and other ICS software. A common thread is that all of these attacks are either known or suspected to have been carried out or supported by nation-states to further political goals, and such activity appears to be on the rise. In a particularly disturbing ICS-targeted attack in 2017, a virus called Trisis or Triton penetrated the safety systems of a Saudi petrochemical plant. Investigation revealed that the attack, which was foiled only by a bug in the computer code, was likely intended to cause an explosion that could have killed and injured people.
Attackers set sights on ICS and third parties
Power companies have long been aware of growing cyber risk, and were one of the first industries to respond, with requirements to implement cybersecurity controls through the North American Electric Reliability Corporation’s Critical Infrastructure Protection (NERC-CIP) standards, initiated in 2007. Nonetheless, the threat continues to evolve, as attackers home in on industrial control systems (ICS) and attempt to access them through third parties in the power sector supply chain.
Targeting ICS blurs line between cyber- and physical attacks: In another unsettling but growing trend, cyberattackers are increasingly targeting industrial control systems (ICS), sometimes potentially laying the groundwork to do physical damage to the grid. Previously, attackers primarily targeted utilities’ information technology (IT) systems to steal data or launch ransomware for financial gain. The threat is now becoming even more insidious, with reports of hackers tied to nation-states and organized crime trying to burrow their way into utility ICS, seeking to learn how systems operate, and positioning themselves to control critical physical assets, such as power plants, substations, transmission, and distribution networks, and to potentially disrupt or destroy them.
This targeting of ICS, which has developed over a decade, is blurring the lines between cyber- and physical attacks, prompting national security concerns in many countries. ICS attacks have evolved in scope and purpose across the globe. Attackers began by exploiting software developed for legitimate purposes, such as Shodan and Metasploit, to find components and devices connected to the internet, and to target supervisory control and data acquisition (SCADA) and other ICS software. A common thread is that all of these attacks are either known or suspected to have been carried out or supported by nation-states to further political goals, and such activity appears to be on the rise. In a particularly disturbing ICS-targeted attack in 2017, a virus called Trisis or Triton penetrated the safety systems of a Saudi petrochemical plant. Investigation revealed that the attack, which was foiled only by a bug in the computer code, was likely intended to cause an explosion that could have killed and injured people.
Against this backdrop of increasing threats to power grids across the globe is a growing source of potential cyber vulnerability—grid modernization. Despite almost limitless advantages to be gained from digitizing and modernizing the grid, modernization can also increase a utility’s “attack surface,” or the number of routes hackers can exploit to enter utility systems. As grids become increasingly “smart,” with information and communications technologies and devices embedded throughout, networks are being linked, the system is gaining complexity, and the number of access points is rising. In addition, as utilities introduce more commonly used software and information technologies into their operations, their systems may become more accessible to adversaries. And, as they increasingly automate functions, the impact of an attack is potentially magnified. Taken together, all of these factors spell increased vulnerability.
Only as strong as its weakest link - Cyber supply chain risk: Power companies used to consider cyber risk in terms of the vulnerability of either IT systems, meaning software, hardware, and technologies that process data and other information, or operational technology (OT) systems, meaning software, hardware, and technologies that help monitor and control physical devices, assets, and processes, including the ICS. In recent years, however, the two systems have been converging as companies digitize and build the power sector’s version of the industrial internet of things, including the “smart grid.” And, as challenging as it may be for power companies to identify their own critical assets and protect them, the challenge seems to be expanding exponentially, since today’s interconnected world also requires them to secure vast, far-flung, and increasingly complex global supply chains.
Power companies purchase information, hardware, software, services, and more from third parties across the globe. And threat actors can introduce compromised components into a system or network, unintentionally or by design, at any point in the system’s life cycle. This may be through software updates or “patches,” which are downloaded frequently, or through firmware that can be manipulated to include malicious codes for exploitation at a later date. Adversaries may also compromise the hardware that utilities install in their operating systems.
In the attack that nearly triggered an explosion and casualties at a Saudi petrochemical plant in 2017, the Trisis or Triton virus was introduced remotely through a brand of controllers used in about 18,000 industrial plants globally. These controllers perform safety functions such as regulating voltage, pressure, and temperatures in nuclear and water treatment facilities, refineries, and chemical plants. The virus was meant to disrupt those functions in the plant. Investigators suggest that although this malware is not highly scalable, the method of attack provides a blueprint for those seeking to corrupt similar equipment elsewhere in the world.
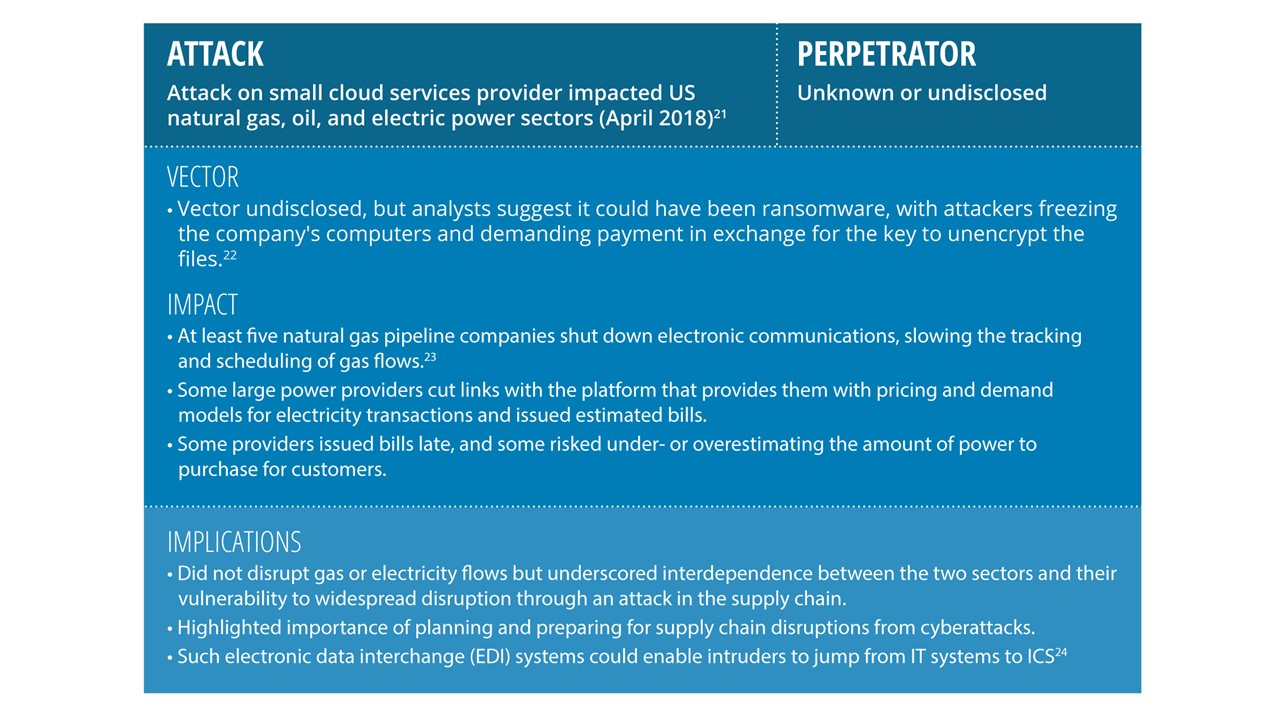
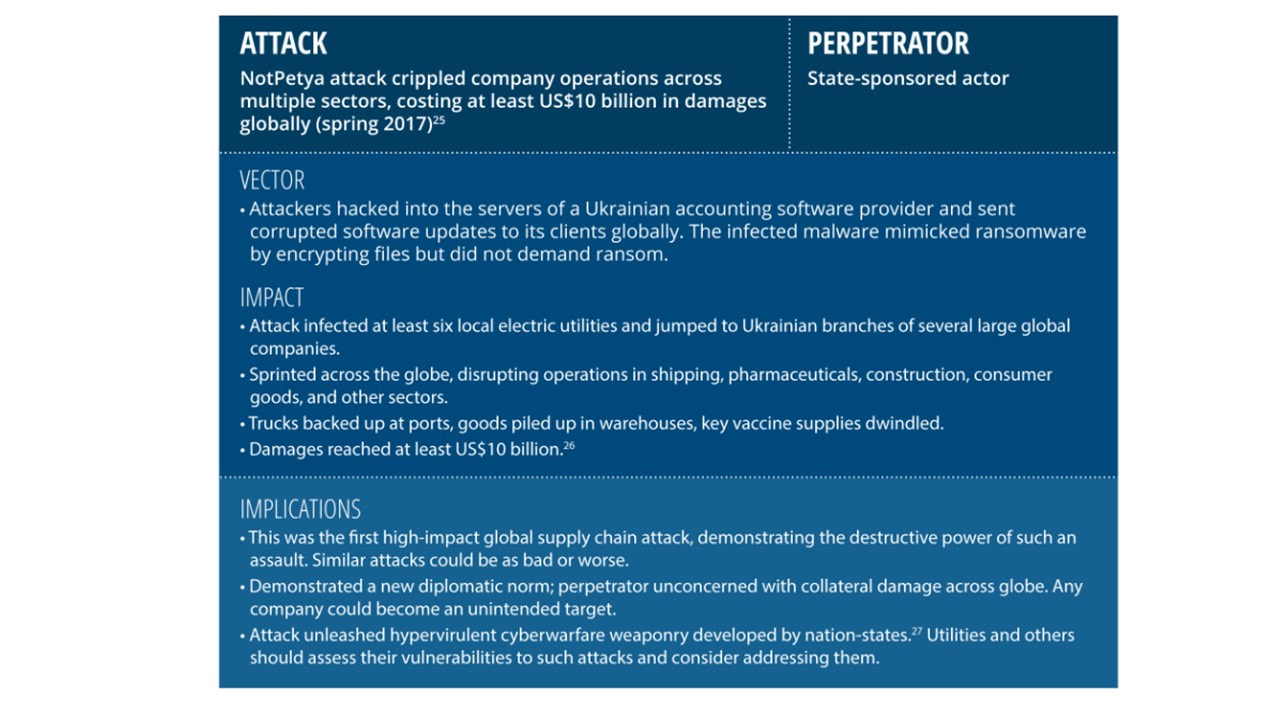
To further explore this threat, figure 3 examines three recent cyberattacks that originated in the supply chain and impacted the power sector. Two of them targeted ICS specifically, and the third targeted IT systems. Alarmingly, all three appeared bent on immediate or potential future disruption rather than financial gain.
Only as strong as its weakest link - Cyber supply chain risk: Power companies used to consider cyber risk in terms of the vulnerability of either IT systems, meaning software, hardware, and technologies that process data and other information, or operational technology (OT) systems, meaning software, hardware, and technologies that help monitor and control physical devices, assets, and processes, including the ICS. In recent years, however, the two systems have been converging as companies digitize and build the power sector’s version of the industrial internet of things, including the “smart grid.” And, as challenging as it may be for power companies to identify their own critical assets and protect them, the challenge seems to be expanding exponentially, since today’s interconnected world also requires them to secure vast, far-flung, and increasingly complex global supply chains.
Power companies purchase information, hardware, software, services, and more from third parties across the globe. And threat actors can introduce compromised components into a system or network, unintentionally or by design, at any point in the system’s life cycle. This may be through software updates or “patches,” which are downloaded frequently, or through firmware that can be manipulated to include malicious codes for exploitation at a later date. Adversaries may also compromise the hardware that utilities install in their operating systems.
In the attack that nearly triggered an explosion and casualties at a Saudi petrochemical plant in 2017, the Trisis or Triton virus was introduced remotely through a brand of controllers used in about 18,000 industrial plants globally. These controllers perform safety functions such as regulating voltage, pressure, and temperatures in nuclear and water treatment facilities, refineries, and chemical plants. The virus was meant to disrupt those functions in the plant. Investigators suggest that although this malware is not highly scalable, the method of attack provides a blueprint for those seeking to corrupt similar equipment elsewhere in the world.
To further explore this threat, figure 3 examines three recent cyberattacks that originated in the supply chain and impacted the power sector. Two of them targeted ICS specifically, and the third targeted IT systems. Alarmingly, all three appeared bent on immediate or potential future disruption rather than financial gain.
When it comes to reducing cyber risk in the supply chain, companies in the power sector face many challenges
First, cyber supply chain accountability and ownership typically do not fall into well-defined, specific groups within a company. They may touch diverse departments, including supply and procurement, corporate information security, cloud and infrastructure, legal, IT, and OT. Most CISOs have no control over the enterprise’s supply chain, and may have little access to supply chain cyber risk intelligence. To mitigate cyber supply chain risk, ownership and accountability should be clearly established.
Second, the business may be pressuring managers to increasingly move operations out to the cloud before they can determine whether the provider is secure. However, companies often have scant visibility into suppliers’ risk management processes and what those processes imply for their own operations. Given sufficient time, they can analyze the potential impact of a cyberattack and map, plan, and build resilient solutions. This should be done before moving operations to the cloud, especially data and energy management systems that could impact reliability if hacked.
Another frequent challenge is the lack of manpower, especially given the overwhelming number of suppliers that should be assessed. A study of 20 electric and gas utilities in North America revealed that the utilities had on average 3,647 total active suppliers, 39 strategic relationships, and 140 suppliers that accounted for 80 percent of their total external spend. Companies may be unable to get access to some suppliers, and some suppliers may be unable or unwilling to adopt secure practices. In addition, certain types of potential cyberthreats can “walk past” controls, such as supply chain firmware updates. Today, most power companies have little control over what suppliers are doing; they’re just beginning to make suppliers more aware and accountable, and to demand supplier integrity.
Nonetheless, there’s hope. There are several steps that companies can take to address cyber risk, particularly in the supply chain.
First, cyber supply chain accountability and ownership typically do not fall into well-defined, specific groups within a company. They may touch diverse departments, including supply and procurement, corporate information security, cloud and infrastructure, legal, IT, and OT. Most CISOs have no control over the enterprise’s supply chain, and may have little access to supply chain cyber risk intelligence. To mitigate cyber supply chain risk, ownership and accountability should be clearly established.
Second, the business may be pressuring managers to increasingly move operations out to the cloud before they can determine whether the provider is secure. However, companies often have scant visibility into suppliers’ risk management processes and what those processes imply for their own operations. Given sufficient time, they can analyze the potential impact of a cyberattack and map, plan, and build resilient solutions. This should be done before moving operations to the cloud, especially data and energy management systems that could impact reliability if hacked.
Another frequent challenge is the lack of manpower, especially given the overwhelming number of suppliers that should be assessed. A study of 20 electric and gas utilities in North America revealed that the utilities had on average 3,647 total active suppliers, 39 strategic relationships, and 140 suppliers that accounted for 80 percent of their total external spend. Companies may be unable to get access to some suppliers, and some suppliers may be unable or unwilling to adopt secure practices. In addition, certain types of potential cyberthreats can “walk past” controls, such as supply chain firmware updates. Today, most power companies have little control over what suppliers are doing; they’re just beginning to make suppliers more aware and accountable, and to demand supplier integrity.
Nonetheless, there’s hope. There are several steps that companies can take to address cyber risk, particularly in the supply chain.
Copyright © 2019 Deloitte Development LLC. This is an excerpt from the original article, "Managing cyber risk in the electric power sector: Emerging threats to supply chain and industrial control systems." For Deloitte's recommended steps, please see the original article.