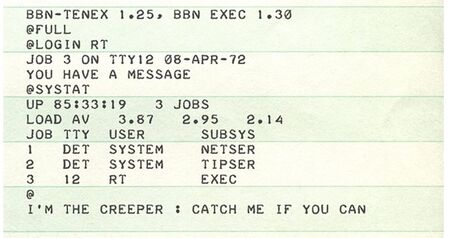
The history of cyber security began with a research project. A man named Bob Thomas realized that it was possible for a computer program to move across a network, leaving a small trail wherever it went. He named the program Creeper, and designed it to travel between Tenex terminals on the early ARPANET, printing the message "I'M THE CREEPER: CATCH ME IF YOU CAN.”
|
A man named Ray Tomlinson (yes, the same guy who invented email) saw this idea and liked it. He tinkered with the program and made it self-replicating – the first computer worm. Then he wrote another program – Reaper, the first antivirus software – which would chase Creeper and delete it. It’s ironic to look back from where we are now, in an era of ransomware, faceless malware, and nation-state attacks, and realize that the antecedents to this problem were less harmful than simple graffiti. How did we get from there to here?
|
From an Academic Beginning, a Quick Turn to Criminality
First of all, let’s be clear – for much of the 70s and 80s, threats to computer security were clear and present. But these threats were in the form of malicious insiders reading documents they shouldn’t. The practice of computer security revolving around governance risk and compliance (GRC) therefore evolved separately from the history of computer security software.
Network breaches and malware did exist and were used for malicious ends during the early history of computers, however. The Russians, for example, quickly began to deploy cyberpower as a weapon. In 1986, the German computer hacker Marcus Hess hacked an internet gateway in Berkeley, and used that connection to piggyback on the Arpanet. He hacked 400 military computers, including mainframes at the Pentagon, with the intent of selling their secrets to the KGB. He was only caught when an astronomer named Clifford Stoll detected the intrusion and deployed a honeypot technique.
At this point in the history of cyber security, computer viruses began to become less of an academic prank, and more of a serious threat. Increasing network connectivity meant that viruses like the Morris worm nearly wiped out the early internet, which began to spur the creation of the first antivirus software.
History of Cyber Security: The Morris Worm, and the Viral Era
Late in 1988, a man named Robert Morris had an idea: he wanted to gauge the size of the internet. To do this, he wrote a program designed to propagate across networks, infiltrate Unix terminals using a known bug, and then copy itself. This last instruction proved to be a mistake. The Morris worm replicated so aggressively that the early internet slowed to a crawl, causing untold damage. The worm had effects that lasted beyond an internet slowdown. For one thing, Robert Morris became the first person successfully charged under the Computer Fraud and Abuse Act (although this ended happily for him – he’s currently a tenured professor at MIT). More importantly, this act also led to the formation of the Computer Emergency Response Team (the precursor to US-CERT), which functions as a nonprofit research center for systemic issues that might affect the internet as a whole.
The Morris worm appears to have been the start of something. After the Morris worm, viruses started getting deadlier and deadlier, affecting more and more systems. It seems as though the worm presaged the era of massive internet outages in which we live. This coincided with the rise of antivirus as a commodity – 1987 saw the release of the first dedicated antivirus company. The Morris worm also brought with it one last irony. The worm took advantage of the sendmail function in Unix, which was related to the email function originally created by Ray Tomlinson. In other words, the world’s first famous virus took at advantage of the first virus author’s most famous creation.
The Rise of the AV Industry
A trickle of security solutions began appearing in the late 80s but the early 90s saw an explosion of companies offering AV scanners. These products scanned all the binaries on a given system and tested them against a database of “signatures”. These were initially just computed hashes of the file, but later they also involved searching for a list of strings typically found in the malware.
These early attempts at solving the malware problem were beset with two crucial problems that were never entirely solved: false positives and intensive resource use, with the latter being a major cause of user frustration as the AV scanner often interfered with user productivity. At the same time, the number of malware samples being produced exploded. From a few tens of thousands of known samples in the early 90s, the figure reached around 5 million new samples every year by 2007. By 2014, it was estimated that around 500,000 unique malware samples were being produced every day. The (by now) legacy AV solutions were swamped: they simply couldn’t write signatures fast enough to keep up with the problem. A new approach was needed.
Endpoint Protection Platforms were the next step. Instead of relying on static signatures to identify viruses, they introduced the use of signatures scanning for “malware families”. The fact that most malware samples are a deviation of existing samples worked well for EPP solutions, as they were able to prove to customers they could prevent the “unknown,” which was in fact detections based on existing malware that their signatures could recognize.
EternalBlue: Lateral Movement Comes to Play
Lateral movement techniques are ways for attackers to issue commands, run code and spread across the network. These are not new to most sysadmins, but thanks to a leak of NSA hacking tools, it turns out that some operating system protocols have had vulnerabilities in them for many years that allow attackers to achieve stealthy lateral movement. One notable example is what we now know as “EternalBlue”. EternalBlue exploits the SMB protocol used for file sharing over the network. This makes the protocol highly attractive to adversaries. EternalBlue was leaked by the Shadow Brokers hacker group on April 14, 2017, and was used as part of the worldwide WannaCry ransomware attack on May 12, 2017. The exploit was also used to help carry out the 2017 NotPetya cyberattack on June 27, 2017 and reportedly is used as part of the Retefe banking trojan since at least September 5, 2017. No Anti-Virus or even next generation EPP can effectively prevent exploitation using EternalBlue.
Fileless malware and system vulnerabilities are just two of a number of common ways that attackers can bypass traditional antivirus (and also more than a few “next-gen” endpoint solutions). So if your company reputation is on the line and you can’t guarantee protection, what can you do? That’s right. You find ways to make sure you are aware of what’s going on with your assets. The new name of the game is Detection.
How Attacks Are Seen Today
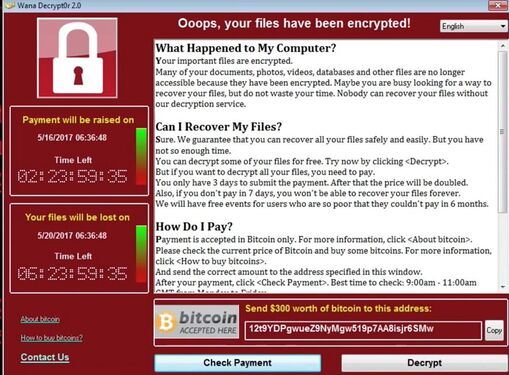
It didn’t take long for adversaries to figure out how to defeat EPP solutions. Fileless malware leveraging built-in tools like VBScript, PowerShell, Office Macros and DDE attack can easily avoid signature-based EPP solutions. This was proved with devastating effect by WannaCry.
It’s hard to recall a bigger shock to the IT community than WannaCry, “the biggest ransomware offensive in history.” Within 24 hours, WannaCry had infected more than 230,000 computers in over 150 countries. From a technical point-of-view, it was not particularly sophisticated. In fact, it exploited a vulnerability that had been known for 91 days and that had already been patched by Microsoft. Even so, an estimated 1.3 billion endpoints were eventually infected. In the UK, the National Health Service – a major client for Sophos – had to cancel 20,000 appointments and operations due to the ransomware. Whether any lives were lost as a result of it will never be known, but what is known is that it crippled the country’s health service.
It’s hard to recall a bigger shock to the IT community than WannaCry, “the biggest ransomware offensive in history.” Within 24 hours, WannaCry had infected more than 230,000 computers in over 150 countries. From a technical point-of-view, it was not particularly sophisticated. In fact, it exploited a vulnerability that had been known for 91 days and that had already been patched by Microsoft. Even so, an estimated 1.3 billion endpoints were eventually infected. In the UK, the National Health Service – a major client for Sophos – had to cancel 20,000 appointments and operations due to the ransomware. Whether any lives were lost as a result of it will never be known, but what is known is that it crippled the country’s health service.
WannaCry is the most famous, but hardly the only case. We see on a regular basis how attackers are finding new ways to compromise devices. A few more examples:
If board members weren’t paying enough attention to the need for better cyber security defenses before, they certainly are now. Additionally, changes in regulation and compliance requirements – alongside a better understanding of the potential reputational risk of a breach – has highlighted why security must be top of the agenda, not just for the board, but for every employee and supplier.
With this in mind, there have been three key shifts have taken place in the wake of recent large-scale cyberattacks:
Security has moved beyond IT
No longer just the concern of the IT geek in the backroom, security now impacts everyone and has an expansive view. Its horizon is absolutely linked to business operations – whether local, regional or even global – and every department it touches. It has the power to break down the silos that enterprises often operate within; increasing interaction across departments, so that assets that need protecting are identified, reducing the impact of a future attack.
However, its reach stretches beyond the confines of the core of the business, out to the edge where data (held in the cloud, on mobile devices and generated by IoT) is in transit and potentially a moving cyber target. Adaptive enterprises are leveraging digital transformation and that impacts how they also use security – linking it back to business objectives; enabling disruptive business models such as mobile banking, and strengthening their focus on cyber threats.
Security is at the heart of innovation
IT security is no longer a barrier to change, hindering the adoption of new processes and the adoption of innovative technologies. In fact, security is front and center in the new digital world. It is accelerating ‘speed of service’; embedded in software-defined networks (SDN); enabling wider, seamless and secure access to data in the Internet of Things (IoT) and much more. Security is now a pre-requisite, built into new technologies and devices from the outset.
Security is becoming smarter, better, faster stronger
Speed and agility are not the only assets IT security needs to harness. It also needs to act smarter and be more effective, often in the face of reduced budgets. Managing security in the digital world involves the gathering, synthesis and analysis of security data as standard. It’s no longer just about the data, but what the data can tell us. Those providers that can leverage insight, intelligence services within a global network view will be at the forefront of the next generation of security services, improving cyber threat visibility and mitigating risk. This will separate the security intelligence provider market into those who just collect data, and those with the foresight and expertise to deliver intelligent insights.
Where do businesses go from here?
It’s impossible to predict exactly where the industry will turn next, but we do know that innovation and digitization will not stop anytime soon. They will continue to grow at an exponential pace, and remain crucial for business success. With this in mind, businesses must embrace new technologies, define strategies that deliver (and exceed) on customer experience, and take a proactive security approach to ensure all these elements can take place securely. Verizon’s 2017 Data Breach Investigations Report showed that the same threat tactics are still effective in infiltrating data, because many organizations are missing a core foundation of security tools and processes.
Given the threat from cybercrime is increasing, businesses can’t afford to be reactive anymore. To succeed in security, they must look towards improving their cyber security systems, as there is too much at stake – no one wants to become a victim of the next WannaCry or NotPetya.
- Using a PowerPoint to run malicious code
- Using a Microsoft Word to run malicious code
- Installing trojans that can use your computer resources to mine cryptocurrency
- Using email spam to trick users
If board members weren’t paying enough attention to the need for better cyber security defenses before, they certainly are now. Additionally, changes in regulation and compliance requirements – alongside a better understanding of the potential reputational risk of a breach – has highlighted why security must be top of the agenda, not just for the board, but for every employee and supplier.
With this in mind, there have been three key shifts have taken place in the wake of recent large-scale cyberattacks:
Security has moved beyond IT
No longer just the concern of the IT geek in the backroom, security now impacts everyone and has an expansive view. Its horizon is absolutely linked to business operations – whether local, regional or even global – and every department it touches. It has the power to break down the silos that enterprises often operate within; increasing interaction across departments, so that assets that need protecting are identified, reducing the impact of a future attack.
However, its reach stretches beyond the confines of the core of the business, out to the edge where data (held in the cloud, on mobile devices and generated by IoT) is in transit and potentially a moving cyber target. Adaptive enterprises are leveraging digital transformation and that impacts how they also use security – linking it back to business objectives; enabling disruptive business models such as mobile banking, and strengthening their focus on cyber threats.
Security is at the heart of innovation
IT security is no longer a barrier to change, hindering the adoption of new processes and the adoption of innovative technologies. In fact, security is front and center in the new digital world. It is accelerating ‘speed of service’; embedded in software-defined networks (SDN); enabling wider, seamless and secure access to data in the Internet of Things (IoT) and much more. Security is now a pre-requisite, built into new technologies and devices from the outset.
Security is becoming smarter, better, faster stronger
Speed and agility are not the only assets IT security needs to harness. It also needs to act smarter and be more effective, often in the face of reduced budgets. Managing security in the digital world involves the gathering, synthesis and analysis of security data as standard. It’s no longer just about the data, but what the data can tell us. Those providers that can leverage insight, intelligence services within a global network view will be at the forefront of the next generation of security services, improving cyber threat visibility and mitigating risk. This will separate the security intelligence provider market into those who just collect data, and those with the foresight and expertise to deliver intelligent insights.
Where do businesses go from here?
It’s impossible to predict exactly where the industry will turn next, but we do know that innovation and digitization will not stop anytime soon. They will continue to grow at an exponential pace, and remain crucial for business success. With this in mind, businesses must embrace new technologies, define strategies that deliver (and exceed) on customer experience, and take a proactive security approach to ensure all these elements can take place securely. Verizon’s 2017 Data Breach Investigations Report showed that the same threat tactics are still effective in infiltrating data, because many organizations are missing a core foundation of security tools and processes.
Given the threat from cybercrime is increasing, businesses can’t afford to be reactive anymore. To succeed in security, they must look towards improving their cyber security systems, as there is too much at stake – no one wants to become a victim of the next WannaCry or NotPetya.